NIST CSF vs NIST SP 800-83: What's the Difference, and Which Framework Fits Your Cybersecurity Strategy?
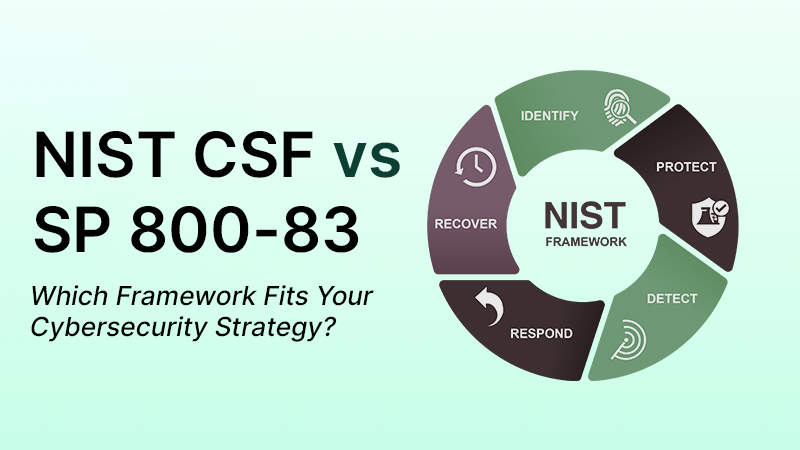
Let’s start with the classic. The NIST Cybersecurity Framework (CSF) is basically the Marie Kondo of security strategy. It helps you figure out what to protect, how to protect it, how to spot trouble, how to handle it, and how to bounce back after everything goes sideways.
Here’s the scene, one that might be familiar for a lot of companies right now. Your team just got asked to prove your cybersecurity is “robust.” Whatever that means. Your client drops a few acronyms: NIST CSF, maybe SP 800-53, or even NIST SP 800-83. Someone in the room Googles it. Someone else slumps into their chair.
If you’ve ever thought: “Why are there so many versions of NIST anything?” you’re in the right place. This guide is your shortcut to decoding two frameworks that often get tossed around like they mean the same thing. Spoiler: they don’t.
We’ll break down what NIST CSF actually is (beyond the five verbs everyone repeats), how NIST SP 800-83 fits into the picture, and how smart companies are using both to tighten up their security game, without losing their minds.
What is NIST CSF? The Basics
Let’s start with the classic. The NIST Cybersecurity Framework (CSF) is basically the Marie Kondo of security strategy. It helps you figure out what to protect, how to protect it, how to spot trouble, how to handle it, and how to bounce back after everything goes sideways.
This isn’t a checklist. It’s a mindset. NIST CSF is built around five core functions that you’ve probably seen in some expensive-looking PowerPoint:
Identify: What do you have that hackers would want?
Protect: What’s stopping them from getting it?
Detect: Would you even know if they did?
Respond: Can you fix it fast without panic-GIFs in Slack?
Recover: How do you get back to business with minimal swearing?
The beauty? It’s flexible. There’s no certification. No audit. No bureaucratic red tape. You decide your level of ambition. Just you, your risk profile, and your to-do list.
Oh, and in 2024, NIST dropped version 2.0 of CSF, adding a new function: Govern. Because it turns out someone actually has to own this stuff.
So What’s NIST SP 800-83, and Why Is It So Specific?
If NIST CSF is your high-level strategy coach, then NIST SP 800-83 is the threat intel nerd who shows up with malware samples and a notebook full of incident playbooks.
NIST SP 800-83 is officially titled “Guide to Malware Incident Prevention and Handling for Desktops and Laptops.” Catchy, right? It’s basically a deep dive into malware, how to spot it, stop it, and recover from it without setting your network on fire.
It gives you play-by-play advice on:
Locking down endpoints (that’s laptops and desktops, not just the fancy stuff)
Avoiding infections in the first place (with layered defenses)
Running response plans that don’t involve unplugging the server rack mid-crisis
While the document was last updated in 2013, the principles still hold up. The malware got fancier, sure, but teaching your team how to handle threats like pros? Still very much relevant.
Really, you don’t choose between NIST CSF and SP 800-83. You combine them. CSF sets the vision. SP 800-83 handles one of the most common threats to that vision. Think roadmap + road hazard manual.
NIST CSF vs. SP 800-83: How They Compare
Let’s not pretend this isn’t confusing. Both NIST CSF and NIST SP 800-83 come from the same institution, both claim to help you get better at cybersecurity, and neither comes with a certificate or badge at the end. So it’s fair to wonder: are they doing the same job?
Not even close.
They have a shared mission: make organizations more resilient, but how they go about it is wildly different. Think of them as two musicians in the same band. One writes the big picture arrangement, makes sure everything is in tune, and sets the rhythm. The other shows up, shreds a solo, and nails the technical details most people miss.
NIST CSF vs SP 800-83: Where They Align
Both NIST CSF and SP 800-83 take a risk-based approach. You won’t find strict checklists or mandated products here. Instead, they ask the most important question in cybersecurity: “What’s most likely to go wrong, and what can you do about it before it does?”
This philosophy runs deep in both frameworks. CSF introduces it at a strategic level, setting a structure across functions like Identify, Protect, Detect, Respond, and Recover. SP 800-83 picks up that thread and gets tactical, especially in areas like malware detection and incident response.
And while they operate at different altitudes, both frameworks are intentionally technology-agnostic. Whether you’re running a legacy data center or a zero-trust Kubernetes cloud, they’re designed to meet you where you are.
That flexibility is exactly why these frameworks have aged so well, even SP 800-83, which hasn’t seen a formal update in over a decade but still reads like it was written for today’s ransomware-riddled reality.
Most importantly, both are practical. They weren’t written by a committee trying to sound smart. They were written by security pros who know exactly how much chaos is involved in real-world incident handling. CSF is strategic. SP 800-83 is gritty. But both are grounded in making cybersecurity doable for actual teams.
NIST CSF vs SP 800-83: Where They Diverge
So, where are the major differences?
Starting simple, NIST CSF is a top-down framework. It’s designed for leaders, CISOs, CIOs, risk officers who need to align an entire organization around cybersecurity. It’s about planning and maturing, not reacting. The language is high-level. The guidance is directional. The goal is clarity and control. SP 800-83 lives in the trenches.
It’s for the people responding to alerts, pushing patches, and building incident response plans that actually work at 2 a.m. It assumes things will go wrong, and offers a step-by-step guide for dealing with it when they do. The guidance is detailed, specific, and technical. You’ll find recommendations for everything from antivirus tuning to how to isolate infected devices without triggering panic.
So while CSF is laying out the strategy in the boardroom, SP 800-83 is walking someone through isolating a compromised laptop and getting it back online without nuking the whole subnet.
The style difference is also striking. CSF reads like a roadmap. It offers functions, categories, and subcategories. It gives you freedom to tailor your approach. SP 800-83 reads like a field manual. There are no maturity tiers or profiles. It’s "here’s what to do" in black and white.
And then there’s auditability. Neither framework is formally certifiable, but CSF is often used as a talking point in audits and board meetings. It gives you a structure for self-assessment and tracking progress over time. SP 800-83 is more about operational proof. You won’t wave it in front of investors, but you’ll use it to show auditors your malware response plan doesn’t rely on hope.
NIST CSF vs SP 800-83: How They Work Together
So, NIST CSF vs SP 800-83: Which do you need? Well, probably both.
The smart move isn’t to pick one. It’s to start with NIST CSF, lay your foundation, build your roadmap, create alignment, and then pull in SP 800-83 where you need precision, especially around malware prevention and response.
Let’s say your CSF “Detect” function is feeling a little thin. That’s your cue to dip into SP 800-83. It’ll walk you through how to implement real-time monitoring, how to respond to malware alerts without making things worse, and how to train your team so they don’t click every pop-up that says “urgent security update.”
Or maybe your CSF “Respond” maturity score is low, and your execs are asking if you’re actually ready for a breach. Again, SP 800-83 is your friend. Use its guidance to run tabletop exercises, test containment procedures, and build a response plan that doesn't involve frantic Googling mid-incident.
CSF gives you the 'what'. SP 800-83 gives you the 'how'. You don’t have to choose. You just have to know when to use each, and use a platform like EasyAudit to track both without losing your sanity.
Where NIST SP 800-53 Fits In
Now, let's introduce another player: NIST SP 800-53. This publication provides a comprehensive catalog of security and privacy controls for information systems and organizations. It's like the building code for your cybersecurity house, detailing the specific requirements for each component.
SP 800-53 offers a set of controls that support the development of secure and resilient federal information systems. These controls are the operational, technical, and management standards and guidelines information systems use to maintain confidentiality, integrity, and availability. The guidelines adopt a multi-tiered approach to risk management through control compliance.
While NIST CSF provides a high-level framework, SP 800-53 offers the detailed controls that can be mapped to the CSF's functions and categories. This integration allows organizations to align their strategic cybersecurity objectives with specific, actionable controls.
So Where Do ISO 27001 and SOC 2 Fit into All This?
Right when you think you’ve wrapped your head around NIST CSF, SP 800-83, and SP 800-53, someone walks into your meeting and says: “Wait, aren’t we also doing ISO? And do we need a SOC 2 report?” Cue the collective eye twitch.
Let’s clear it up.
ISO 27001 is the international gold star for information security management. It’s structured, it’s formal, and it comes with a shiny certificate if you play your cards right. Big enterprises love it. Procurement teams practically drool over it.
Meanwhile, SOC 2 is your backstage pass to doing business with anyone who cares about how you handle customer data. It’s especially common in the U.S., and it's all about proving you're secure, available, private, and not running your cloud like a garage sale.
Key Differences in One Breath:
NIST CSF: Strategic, flexible, American-made, no certificate required.
ISO 27001: Formal, global, audit-required, documentation-heavy.
SOC 2: Customer-facing, trust-focused, evidence-based, driven by CPA firms.
A triangle diagram showing CSF = Strategy, ISO = Certification, SOC 2 = Trust & Assurance. Title it: “Pick Your Flavor, or Mix All Three”
These frameworks aren’t mutually exclusive. In fact, they often overlap. You can absolutely use NIST CSF to build your security maturity, SOC 2 to prove it, and ISO 27001 to lock it all in with a bowtie and a binder. This is where EasyAudit starts to shine. More on that in a moment.
Real-World Use Cases: When to Use NIST CSF vs SP 800-83
Okay, let’s take the buzzwords out for a spin.
Use Case #1: The Early-Stage SaaS Startup
You’re a five-person team. You just closed seed. Your customers are enterprise-sized but your compliance program is still conceptual. Your move? Start with NIST CSF. It’s lightweight, flexible, and gets you from “we have no policies” to “we know our risks and are working on them” fast.
Ideal Framework: NIST CSF
Use Case #2: The Fintech Scaleup
You move money. You handle personally identifiable info. Your board just asked what happens if you get hit with ransomware. Time to layer in SP 800-83. Use it to build out your malware prevention plan and sharpen your incident response.
Ideal Frameworks: NIST CSF + SP 800-83
Use Case #3: The Public Sector Contractor
You just won a government contract. Now they’re throwing around words like “FedRAMP” and “CUI.” That’s your cue to go deep into NIST SP 800-53, but with CSF and SP 800-83 giving structure to your daily operations.
Ideal Frameworks: All three (and probably a compliance lead with military-grade patience)
How EasyAudit Makes NIST Frameworks Simple
Here’s the thing about frameworks like NIST CSF, SP 800-83, and SP 800-53: They’re brilliant in theory. They also have a special talent for turning your Google Drive into a graveyard of half-finished policies and draft risk assessments.
This is exactly where EasyAudit steps in.
So What Does EasyAudit Actually Do?
Maps Everything Automatically: Write one control, apply it to NIST CSF, ISO 27001, SOC 2, and beyond. EasyAudit crosswalks your work across frameworks so you're not reinventing the wheel every time a new acronym shows up in your inbox.
Turns Chaos into Checklists: No more “we’ll document it later” moments. The platform gives you real-time dashboards, control ownership, deadlines, and progress tracking, like Monday.com but for grown-up cybersecurity programs.
Automates Evidence Collection: Hook up your stack (AWS, Okta, GitHub, Google Workspace), and EasyAudit pulls evidence automatically. It timestamps everything, organizes it into clean audit folders, and even makes your auditors less grumpy.
AI-Powered Gap Analysis: Answer a few questions, and the system shows you where you’re solid, and where your S3 buckets are still crying out for encryption.
Policy Templates That Don’t Suck: Need an Access Control Policy that actually makes sense? A Malware Response Plan inspired by SP 800-83? Done. Editable. Pre-mapped. No legalese overload.
How to Roll It All Out: A Smart Strategy for Real Humans
So, you’ve got NIST CSF giving you the high-level game plan. You’ve added SP 800-83 to handle malware. Maybe SP 800-53 is showing up in client contracts. What now?
Here’s the Playbook:
Start with CSF: Use the five (okay, now six) core functions to scope your security strategy. Build a current profile and a target profile. Don’t try to boil the ocean.
Layer in SP 800-83: Add this when your team is ready to get specific about endpoint threats. Build your malware playbooks. Run simulations. Prove to stakeholders that your detection and response muscle is real.
Use SP 800-53 as a Control Menu: Pick controls that matter. Skip the ones that don’t. With EasyAudit, mapping is automatic and painless, so there’s no need to get stuck in control spreadsheet hell.
Track It. Prove It. Improve It.: Compliance isn’t just a “check-the-box” game. The best teams use platforms like EasyAudit to keep everything running smoothly, policies, ownership, evidence, and progress reports all in one place.
You Don’t Need Another Framework: You Need a Plan
Choosing between NIST CSF vs SP 800-83 isn’t really the point.
You’re not picking between frameworks like you’re choosing between Android and iPhone. You’re building a security system that can actually stand up to modern threats, and help you win business, pass audits, and sleep at night.
The best strategy?
Use NIST CSF to set your foundation.
Use SP 800-83 to get real about malware.
Use EasyAudit to bring it all together.
You don’t have to be a compliance nerd to make this stuff work. You just need the right tools, and a little help. Book a demo and we’ll show you how painless compliance can be.